FBI and CISA Release Ransomware Alert on Vice Society Targeting Education Orgs
Details on TTPs and Mitigation Recommendations Come As CISA and FBI Help Investigate Los Angeles Schools' Weekend Ransomware Attack
- By Kristal Kuykendall
- 09/06/22
A joint Cybersecurity Advisory released today by the FBI, Cybersecurity and Infrastructure Security Agency, and Multi-State Information Sharing and Analysis Center — as those agencies help investigate the Labor Day weekend ransomware attack on Los Angeles Unified School District — warns that Vice Society threat actors are disproportionately targeting the education sector as recently as this month.
Such so-called #StopRansomware advisories describe observed tactics, techniques, and procedures as well as indicators of compromise to help organizations protect themselves against the newest ransomware threats.
“The FBI, CISA, and the MS-ISAC anticipate attacks may increase as the 2022/2023 school year begins and criminal ransomware groups perceive opportunities for successful attacks,” the advisory states. “School districts with limited cybersecurity capabilities and constrained resources are often the most vulnerable; however, the opportunistic targeting often seen with cyber criminals can still put school districts with robust cybersecurity programs at risk. K–12 institutions may be seen as particularly lucrative targets due to the amount of sensitive student data accessible through school systems or their managed service providers.”
The advisory includes technical details of the Vice Society TTPs, using the MITRE ATT&CK® for Enterprise framework, version 11. The technical details included in the advisory are as follows, verbatim from the report (each of which is explained in further detail in the full advisory PDF):
- Vice Society is an intrusion, exfiltration, and extortion hacking group that first appeared in summer 2021. Vice Society actors do not use a ransomware variant of unique origin. Instead, the actors have deployed versions of Hello Kitty/Five Hands and Zeppelin ransomware, but may deploy other variants in the future.
- Vice Society actors likely obtain initial network access through compromised credentials by exploiting internet-facing applications [T1190].
- Prior to deploying ransomware, the actors spend time exploring the network, identifying opportunities to increase accesses, and exfiltrating data [TA0010] for double extortion — a tactic whereby actors threaten to publicly release sensitive data unless a victim pays a ransom.
- Vice Society actors have been observed using a variety of tools, including SystemBC, PowerShell Empire, and Cobalt Strike to move laterally. They have also used “living off the land” techniques targeting the legitimate Windows Management Instrumentation (WMI) service [T1047] and tainting shared content [T1080].
- Vice Society actors have been observed exploiting the PrintNightmare vulnerability (CVE-2021-1675 and CVE-2021-34527) to escalate privileges [T1068]. To maintain persistence, the criminal actors have been observed leveraging scheduled tasks [T1053], creating undocumented autostart Registry keys [T1547.001], and pointing legitimate services to their custom malicious dynamic link libraries through a tactic known as DLL side-loading [T1574.002].
- Vice Society actors attempt to evade detection through masquerading their malware and tools as legitimate files [T1036], using process injection [T1055], and likely use evasion techniques to defeat automated dynamic analysis [T1497].
- Vice Society actors have been observed escalating privileges, then gaining access to domain administrator accounts, and running scripts to change the passwords of victims’ network accounts to prevent the victim from remediating.
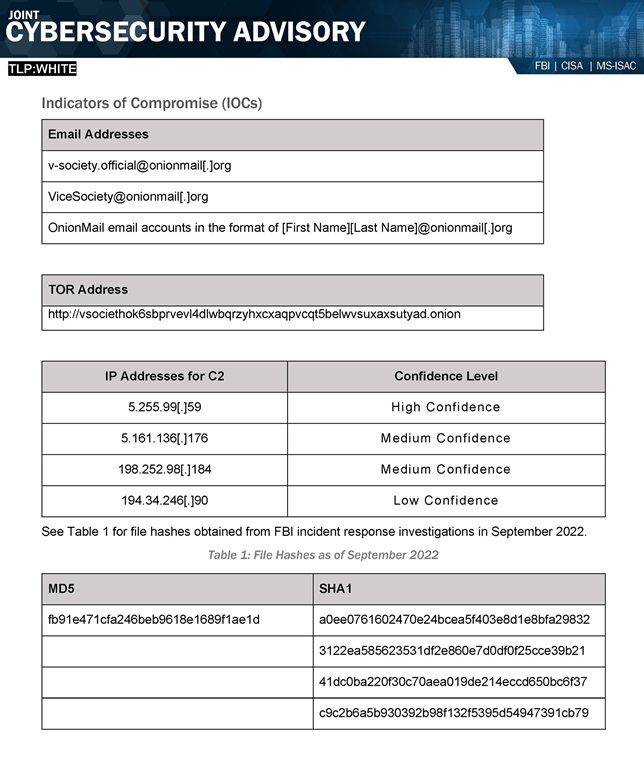
The advisory also lists specific Indicators of Compromise such as email addresses, TOR addresses, IP addresses, and file hashes for IT practitioners to be on the lookout for, pictured below.
Mitigation recommendations make up the last three pages of the advisory, along with a reminder that “all organizations should report incidents and anomalous activity to CISA’s 24/7 Operations Center at [email protected] or (888) 282-0870 and/or to the FBI via your local FBI field. State, local, tribal, and territorial (SLTT) organizations should report incidents to MS-ISAC (866-787-4722 or [email protected]). When available, please include the following information regarding the incident: date, time, and location of the incident; type of activity; number of people affected; type of equipment used for the activity; the name of the submitting company or organization; and a designated point of contact.”
The advisory emphasized that the FBI is seeking “any information that can be shared, to include boundary logs showing communication to and from foreign IP addresses, a sample ransom note, communications with Vice Society actors, Bitcoin wallet information, decryptor files, and/or a benign sample of an encrypted file.”
About the Author
Kristal Kuykendall is editor, 1105 Media Education Group. She can
be reached at [email protected].