Report Details Increasingly Sophisticated Phishing Attacks and Proxies Targeting Students
Monthlong Test of PhishID Reveals New Methods That Get Around Traditional Detection, Content Filters
- By Kristal Kuykendall
- 02/23/23
In a monthlong study of one U.S. school district with newly implemented PhishID security software, Identity Automation uncovered detailed markers of increasingly sophisticated phishing attacks and dangerous proxy services targeting students, according to a new report out from Identity Automation.
The cybersecurity company, which introduced its RapidIdentity PhishID solution last summer, conducted the study in January, closely monitoring infrastructure security and attempted threats for the first 30 days after the district “turned on” its new anti-phishing software, the report said.
During that time, PhishID “detected and blocked a total of 73 malicious sites that were clicked by students and staff, including brand new phishing attacks and dangerous proxy services targeted to students,” according to the report. PhishID is powered by PIXM technology and uses AI computer vision to detect phishing attacks and unsafe proxy sites, Identity Automation said.
“While the K–12 sector is focused on preventing account takeovers leading to ransomware attacks (and rightfully so), a less well-known threat is targeting our students: account takeovers leading to the identity theft of students and minors. These types of targeted phishing campaigns dupe students into voluntarily offering their credentials,” said Identity Automation in its report, citing a study showing that one in 50 children had their identity stolen in 2021. “Unlike adults, students are a ‘blank slate’ for identity thieves. They don’t have credit reports and few parents actively monitor their child’s credit or SSN — meaning the fraud can go undetected for years. Malicious actors use students’ stolen credentials to then access their individual PII for valuable information, like a Social Security number with no credit score. Further, these attacks often occur without the end-user or administrators ever becoming aware that the incursion has taken place.”
The district — not named in the report — had previously implemented Identity Automation’s RapidIdentity access management platform for K–12 schools, and it had just added PhishID to its cyber risk management strategy, according to the report. Since the study was completed, the district has also further expanded on its cyber protections, adding multi-factor authentication, the report noted.
The study and its results offer K–12 IT and security practitioners valuable insight into threat actors’ most-used methods and ways school districts can protect student and staff and their data.
Key Findings: 30 Days of Phishing Attacks at a School
- Students are the target: “Student accounts are being targeted to gain access to their valuable personal identifiable information and their “blank slate” credit history for the purposes of identity theft and ultimately, financial gain,” the report said.
- Sophisticated, student-specificphishing: Students are targeted via emails containing links that appear to have school-related content, or the emails look like a legitimate service popular with students such as an educational site or video game — but the links actually take the students to spoofed login pages where credentials and other sensitive data can be easily intercepted and stolen, Identity Automation said.
- Evasion tactics in use: Such phishing attacks and dangerous proxy services “are extremely difficult to detect and stop by traditional means due to stealthy tactics, such as quick deploy web applications and proxy aware connections,” the report said.
- Stealthy features circumvent content filters: Malicious sites are using URL cloaking and tab cloaking features — or requiring site visitors to use them to “log in” to “their website” that is actually a malicous website — to “circumvent content filters and allow students continued access,” even after the known malicious domain is blacklisted, the report said.
Recommendations to Minimize the Phishing Threat
Identity Automation urged school districts and their IT and security leaders to take the following steps to protect against phishing attacks, verbatim from the report:
-
Don’t assume safeguarding inboxes, content filters, and regular user training are enough to protect students from phishing attacks.
-
Implement advanced anti-phishing protection that uses AI computer vision to detect phishing attempts, regardless of a threat’s origin or stealthy techniques used.
-
Protect your students’ digital identities by enforcing strong and appropriate MFA across ALL user populations — including students.
The report noted that school districts face a big enough challenge deploying MFA for all staff, let alone for students and parents, and said malicious actors are taking advantage of the gap in security, “specifically targeting students by luring them into risky behavior to access the non-district-approved sites they want to go to, and potentially causing long-lasting ramifications for these students once their identities have been stolen and sold.”
Content filters are being bypassed as a matter of course, when students are unaware they are bypassing a content filter to access a site that is actually dangerous and is not the authentic website for the game or content they are accustomed to accessing, the report said. “PhishID’s threat data further reinforces that adversaries are using stealthy techniques to get around content filters, deliver phishing attacks to students, and lure them into dangerous websites and services that are designed to steal data.”
Detailed Findings on Phishing and Proxy Site Tactics
Finding 1: High Phishing Volume
After PhishID was deployed at the district, the software detected a phishing attack clicked by a student within a few hours on Jan. 3, the report said. “As of Jan. 31, PhishID had detected and blocked a total of 73 malicious sites that were clicked by students and staff, including brand new phishing attacks and dangerous proxy services targeted to students,” the report said. “These cases in particular were all undetected by 100% of the entire VirusTotal community.”
Finding 2: Dangerous Proxy Sites
In addition to phishing, dangerous proxy services were also observed, many of which were built specifically to target students and lure them to circumvent school content filters, the report said. “Unfortunately, they also lead students to login pages where their credentials and other sensitive data can be easily intercepted or stored … and allow access to popular chat applications like Discord, where there has been a reported rise in malware delivery, often disguised as legitimate applications or websites.”
Finding 3: Student Targeting
The malicious links detected by PhishID frequently contained references to school related content, such as math, music, or other learning materials, as seen in the following examples:
-
https://binarypiano[.]com/
-
https://studentholiday[.]xyz/~/hvtrs8%2F-aacmultq...
-
http://www[.]kidsmathplay[.]com/
-
https://monstermath[.]herokuapp[.]com/main/https://discord[.]com/login
Finding 4: Tactics That Evade Traditional Detection
The malicious sites identified in the PhishID study evade detection by using a variety of “stealthy means” such as quick-deploy web app services, which are used for a brief period of time and then abandoned before detection services or blacklists catch on, said the report. For example, the following domains detected in the PhishID study were active for less than 24 hours, the report said:
“These services strategically leverage quick deployment technologies, like Herokuapp, so that if one of their proxy sites is taken down, they aren’t required to purchase, register, and configure all of the proxy resources to a new domain,” Identity Automation said. “Instead, when the existing domain gets blocked, a small change is simply made to the domain name and the proxy site is redeployed, becoming accessible again under a slightly different name.”
Identity Automation also reported that the study identified “the tactic of serving malicious content based on the origin of a request.” In the example shown below, “PhishID detected a website that previously hosted educational content but was taken over by a malicious actor,” the report said. “When accessed from a sandbox, it redirects to Google.com. When accessed from an endpoint, however, it redirects to the malicious site intended for the target.”
Finding 5: How Students Evade Content Filters
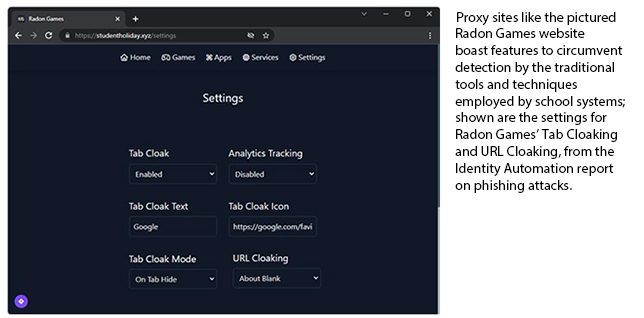
Proxy sites can evade content filters — even if they are blacklisted — because some proxies have embedded “stealthy features” like tab cloaking and URL cloaking that enable students to access blacklisted sites.
“One of the sites we observed is maintained by a group called ‘Radon Games’ which creates gaming websites that offer internet browsing features to enable students to ‘escape internet censorship,’” Identity Automation said, noting that Radon Games is part of group of proxy sites targeting K–12 students called the Titanium Network.
“Radon Games, like many other proxies we have investigated, can be accessed through a variety of domains that appear to change in the event one of them is detected as a proxy site,” the report said. “In our case, it was accessed by a student via studentholiday[.]xyz. The website boasts many features to circumvent detection. Even if the main site is reported as a proxy, the student can use the site’s features to maintain an undetected connection once one has been initiated, by leaving the undetected connection open in a tab.”
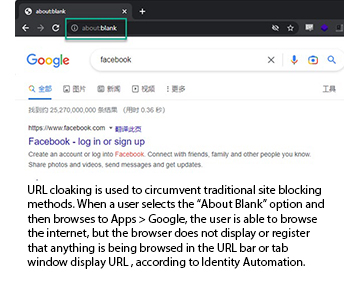 When URL cloaking is enabled on a proxy site, students “can force the browser to not register or display the URL of the site they are visiting,” the report said. Such cloaking circumvents content filters, blacklisting, and browser-based detection solutions. In the below pictured example from the report, “when a user selects the ‘About Blank’ option and then browses to Apps — Google, the user is able to browse the internet, but the browser does not display or register that anything is being browsed in the URL bar or tab window display.”
When URL cloaking is enabled on a proxy site, students “can force the browser to not register or display the URL of the site they are visiting,” the report said. Such cloaking circumvents content filters, blacklisting, and browser-based detection solutions. In the below pictured example from the report, “when a user selects the ‘About Blank’ option and then browses to Apps — Google, the user is able to browse the internet, but the browser does not display or register that anything is being browsed in the URL bar or tab window display.”
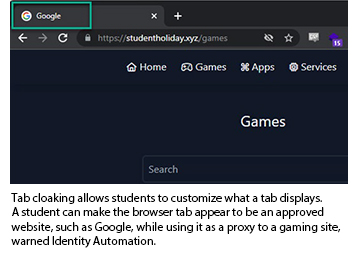
When students enable tab cloaking, they can customize what the tab will display, including the logo of the “website” they want to emulate. “This allows students to make the browser tab appear to be an approved website or service, while using it as a proxy to Discord, YouTube, Google, etc.,” the report said. “In the event a teacher or administrator walks by the student's device and observes the browser tabs, they will not arouse any suspicion that they are visiting anything but school approved websites.”
Identity Automation emphasized the importance of school districts’ proactive protection against phishing and proxy sites — noting that more than half of phishing attacks target victims through social media and chat platforms, and mobile messaging is a growing avenue as well.
The company also urged districts to implement MFA across all user groups, including students.
Read and download the full report at the Identity Automation website.
About the Author
Kristal Kuykendall is editor, 1105 Media Education Group. She can
be reached at [email protected].