Tips Toward a Safe and Positive Social Media Experience
- By Stephen Spengler
- 06/01/17
It is inevitable that our children will seek to create social media accounts, interact with people online, share information, and post day to day activities and thoughts for the world to see. The number of apps, sites and games presented to them are too numerous to even list. For parents, understanding the ins and outs of social media and related sites and apps can be a daunting and never-ending task. This article presents some ideas and suggestions to work towards being a more informed digital parent.
Good Digital Parenting
The Family Online Safety Institute recommends that parents engage in “7 Steps to Good Digital Parenting” to keep abreast of all that is digital in our children’s lives.
1. Talk with your children. Talk to your children about your concerns regarding social media. Start discussing technology, the potential dangers, and what it can be used for at an early age. Remember to be open and honest about the issue. Most elementary schools begin educating children in the primary grades about proper and ethical technology use, so extending the conversation to home can be a great team effort!
2. Educate yourself. Technology moves at the speed of light. New things are developed every day that may or may not be appropriate for your child’s age group. If you do not have firsthand knowledge of an app or website, search for information about it. If an app has been deemed inappropriate or misleading in its function, then parents or advocacy groups are posting online about it! Go ahead and download or install the app on your own device and see for yourself. Sometimes the best approach is to just try it yourself and then you be the judge.
3. Use parental controls. Check the safety controls on all of the Android and Apple devices that your family uses. On the iPhone, you can tap SETTINGS > GENERAL> RESTRICTIONS and you can create a password that allows you enable/disable apps and phone functions. On Android devices, you can turn on Google Play Parental Controls by going into the Google Play Store settings. From there, you can create a parent pin that allows you to filter to age appropriate content and apps. In addition to these two stock features, parents can always purchase, download and install parental monitoring software such as NetNanny, PhoneSherriff, Norton Family Premier and Qustodio. A simple online search for “parental device control” will produce a number of options with ranges of pricing.
4. Friend and follow your children on social media. Whether it’s musical.ly, Instagram or Twitter, chances are that your children use some form of social media. If you have not already, then create an account and get on their friends list. If you are on his or her friends list, then you will see everything that your son or daughter posts, shares, receives and comments on. You will get a good idea of who his or her friends are and what he or she is sharing. Remember to respect their online space and refrain from commenting on posts. Your goal is to review the content and to encourage your children to keep a good digital reputation.
5. Explore, share and celebrate. Just like you may share your love of hiking, sports or hobbies with your children, learn to make the online world one of those, too. Go online and explore the internet with your children. Find apps and sites that you would use a family. Show them that you enjoy the online world and the information and resources available to you at your fingertips. Employ internet-enabled forms of communication with your children and take the time to learn about technology with them. Most of all, demonstrate that a positive Internet experience will assist them later in their digital lives.
6. Be a good digital role model. Now is the time to review your own digital habits, too. The idiom “do as I say, not as I do” does not apply here. Be a digital role model. Begin by spending more time in the physical world by putting down the digital world. Show them that unplugging from devices is just as good, if not better than always having a device attached to your hand. Show them how to be productive technology users by using technology to seek answers to questions, evaluate information and to create products to solve problems.
7. Set ground rules and apply sanctions. Just like chore charts or family job lists, consider using a family social media or internet safety contract. These contracts establish ground rules for when devices are to be used; what they should and should not be doing on them; and to establish sanctions based on breaches of the family contract. A simple internet search for “family internet contract” or “family technology contract” will produce a wealth of available ideas and resources to help you implement rules and sanctions revolving around your family’s technology use. A good example of a social media contract for children can be found at imom.com/printable/social-media-contract-for-kids/. It establishes ground rules for personal internet security; what can be shared and not shared; what to do or not do to be a good digital citizen; and what consequences result from violating the established rules.
Managing Your Digital Footprint
Your digital footprint, according to dictionary.com, is “one's unique set of digital activities, actions, and communications that leave a data trace on the internet or on a computer or other digital device and can identify the particular user or device.” Digital footprints can be either passive or active. The passive digital footprint is created without your consent and is driven by the sites and apps that you visit. The data from a passive digital footprint could reveal one’s internet history, IP address, location and is all stored in files on your device without you knowing it. An active digital footprint is more easily managed by the user. Data from an active digital footprint shows social media postings, information sharing, online purchases and activity usage. Though the passive digital footprint can be almost impossible to manage, the active digital footprint is in total control by the user. It is easily managed through habit and can be cleaned up by adjusting one’s internet activity. To help you, your son or daughter, or other family member clean up one’s digital footprint, the Family Online Safety Institute has some key suggestions for doing so:
- Search for yourself online. Search for your formal first and last name. Also search for slightly different spellings and for nicknames. Review the results. Do they portray you in a positive or professional light? If you find something posted about you in social media that you do not like, follow the trail and request that it be removed. If that route does not work, then reach out to the app or site’s administrators to seek the proper channels for having the content removed. Most social media sites, if operated inside the United States, will permit users to request content to be removed if offensive, inflammatory or incorrect.
- Check privacy settings. Privacy and sharing settings for apps and social media sites change all the time. Keep up to date with the app or site’s settings to see if things have changed regarding privacy, content sharing or validity of content. Invest a little time to understand what the current settings are, so you have no doubt about what you are sharing and what people can see. Be sure to make any changes and update your settings if there are things that you do not want to be public.
- Use strong passwords. It is a good idea to have multiple passwords and to use strong passwords. Whether you are doing online banking or logging into Facebook, change your passwords frequently and use combinations of letters, numbers and symbols. Always avoid combinations of birthdates, anniversaries, or the names of family members or pets. Avoid using dictionary words or strings of dictionary words. Symantec, creators of the Norton Security Suite, suggest using passwords that are at least twelve characters in length; include numbers, symbols, capital letters and lower-case letters; not dictionary words or combination of dictionary words; and do not rely on obvious substitutions such a “0 “for the letter “O.”
- Update software. There is a reason that operating systems such as Chrome OS, Windows, MacOS, iOS, and Android have frequent updates. Computer viruses, spyware and ransomware can cause major damage to your computer, your data and your personal life! Check for updates often and do not ignore them. They are one of the best ways to manage the security on your devices. Updates can even be scheduled to occur automatically without you having to lift a finger.
- Maintain your device. Along with keeping the device or operating system up to date, take the time to understand your device settings. Set passwords to prevent access to the device and to the settings area. Review any apps that you have on the device and read their polices for information sharing. Know your child’s password to all of their devices. Look for apps that share location, personal information and may link to others such as family members or even your children. If the app gives out too much, it is not worth it. Also, delete apps that you do not use. A deleted app is one that will not be able to share your personal information.
- Think before you post. Your digital footprint is not all about what is posted about you on the internet. It also reflects what you post, share and say about others. You should seriously consider what you post online and the potential impact that it may have. A good rule of thumb is to ask yourself if you would want your family or close friends to see what you are about to post. Always think before you post and teach your children to only post things that are true, helpful, inspiring, necessary or kind.
Keep These Apps on Your Radar
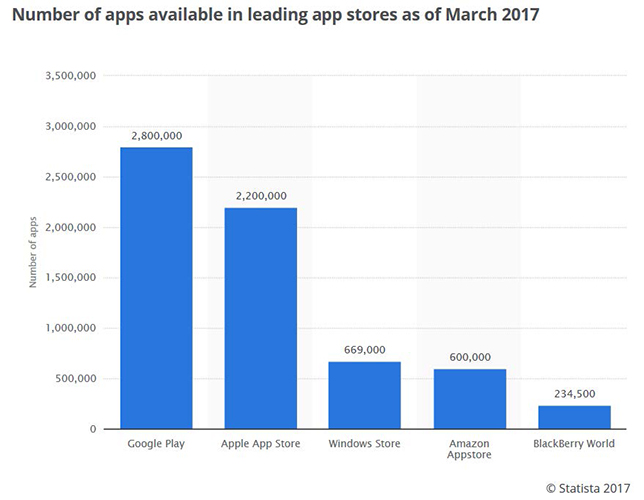
According to The Statistics Portal as of March 2017, there are approximately 2.8 million apps in the Android Play Store and there are approximately 2.2 million in the Apple App Store. That’s over 5 million apps, not including what is available in the Windows Store, Amazon Prime, the Google Chrome App Store, etc. Please understand that not all apps are created equal; not all apps are genuine; and that many apps hold secrets that parents need to know. A simple internet search for “apps parents should know about” will produce a laundry list of apps that are not appropriate for children of any age and often hide serious dangers that we do not want our children to be exposed to. Many times, the minimum age requirements for apps are not followed and younger children end up using the apps. In addition, many apps claim that they are for younger ages, while they end up being child predator hangouts. Though I cannot list every app and each pitfall, here is a short list of apps to keep an eye out for:
• Afterschool (minimum age 17) – The Afterschool App was rejected twice from the major app stores due to complaints from parents and educators. It is a well-known app that promotes cyberbullying, sexting, pornography and is filled with references to drugs and
alcohol.
• Blue Whale (minimum age 10) – IF YOU FIND THIS APP ON YOUR CHILD’S DEVICE, DELETE IT. It is a suicide challenge app that attempts to prod children into killing themselves. It builds trust in children while challenging them to complete tasks. It is a haven for child predators and it is common for children to be blackmailed and bullied into completing the game where a final task is suicide.
• BurnBook (minimum age 18) – IF YOU FIND THIS APP ON YOUR CHILD’S DEVICE, DELETE IT. It is a completely anonymous app for posting text, photos, and audio that promote rumors about other people. It is a notorious for cyberbullying and law enforcement has it on its watchlists.
• Calculator% (minimum age 4) – IF YOU FIND THIS APP ON YOUR CHILD’S DEVICE, DELETE IT. This is one of hundreds of “secret” calculator apps. This app is designed to help students hide photos and videos that they do not want their parents to see. This app looks and functions like a calculator, but students enter a “.”, a 4-digit passcode, and then a “.” again. Once entered, the app owner can take photos with the app or add hidden photos to the photo gallery.
• KIK (minimum age 17) – This is a communications app that allows anyone to be contacted by anyone and it 100 percent bypasses the device’s contacts list. It is very difficult to determine who is a predator and who is not with this app. Though very popular, it is something that you may want to remove from your child’s device.
• Yik Yak (minimum age 18) – This app is a location-based (most commonly schools) bulletin board app. It works anonymously with anyone pretending to be anyone they want. Many schools across the country have encountered cyberbullying and cyberthreats originating from this app. School districts will make every effort to geo-block this app making it 100 percent unusable from any campus location.
• StreetChat (minimum age 14) – StreetChat is a photo-sharing board for middle school, high school and college-age students. Members do not need to be a student in the actual school and can impersonate students in schools across the country. It promotes cyberbullying through anonymous posts and private messaging.
• ooVoo (minimum age 13) – IF YOU FIND THIS APP ON YOUR CHILD’S DEVICE, DELETE IT. ooVoo is one of the largest video and messages app. Parents should be aware that ooVoo is used by predators to contact underage children. The app can allow users to video chat with up to twelve people at one time.
• Wishbone (girls) & Slingshot (boys) (minimum age 13) – Both are comparison apps that allow users to create polls, including ones that are not appropriate for children. Many of the users create polls to shame and cyberbully other children, plus there are inappropriate apps and videos that users are forced to watch via the app’s advertising engine.
Conclusion
The internet is an amazing tool for learning, information seeking and communications. However, it has also become a refuge for predators, inappropriate behavior, cyberbullying and other activity. If knowing is half the battle, then talking about it is the other half. There is no way to know everything about all the dangers lurking on the internet or in apps. There is also no way to know everything our children are doing at all times.
As school districts continue to expand the message of ethical and proper use in their course offerings, it will influence their behavior. If families continue to sit down and discuss these issues, it will also influence their behavior. It is through this partnership of school and home that we will truly assist one another in learning about the potential risks of being social on the internet.