Ransomware Targeting K-12 Grew a Massive 827% Last Year, SonicWall Reports
Malware Attacks Also Rose Significantly as Did Attacks on IoT Devices
- By Kristal Kuykendall
- 04/13/23
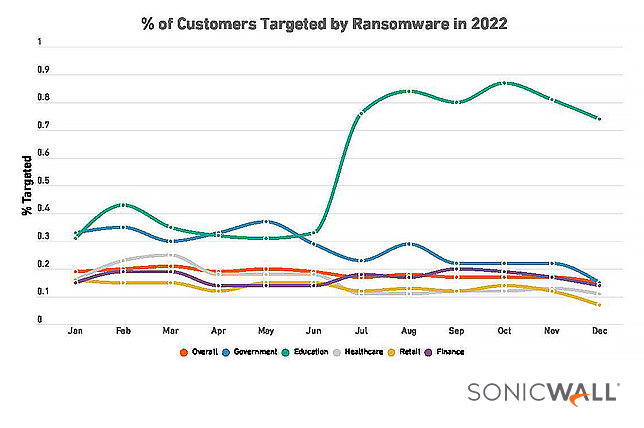
Ransomware attacks targeting K–12 schools worldwide last year grew at an “absolutely massive” rate of 827% over 2021, according to SonicWall’s 2023 Cyber Threat Report, and the data shows that education customers — those whose data is compromised during ransomware attacks — had the highest percentage reporting ransomware attempts of all sectors studied.
Overall, ransomware attacks worldwide decreased in 2022 by about 21% from 2021 totals, SonicWall said in its new report. Ransomware attacks in the United States fell by almost half; yet the United States still experienced the most ransomware attacks by far, with 217.5 million recorded in 2022 — more than three times the No. 2 most-targeted country, the United Kingdom.
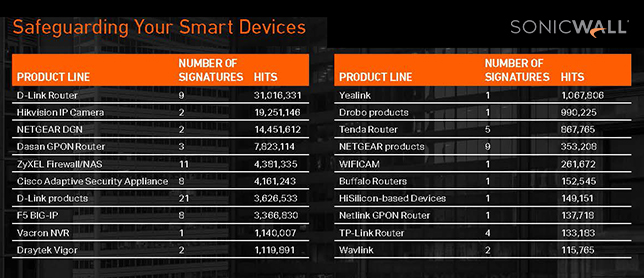
The biggest growth in cyber attack vectors targeting education last year came in the form of encrypted attacks, or malware over HTTPs, rising 411% in the education sector, and as malware targeting Internet of Things or connected smart devices, which rose 169% in the United States and 146% in the education sector specifically, according to SonicWall’s report.
K–12 organizations experienced a 323% rise in malware attacks, SonicWall said, by far the largest increase of all sectors analyzed for the report.
Malware worldwide rose 2% to 5.5 billion reported incidents; intrusion attempts worldwide rose 19% to 6.3 trillion incidents; and IoT malware attacks worldwide were up 87%, SonicWall reported.
“Mounting cyberinsurance requirements and the specter of mandatory reporting offered even more motivation to harden defenses,” the report said. “And in 2022, the U.S. government created the Virtual Asset Exploitation Unit, increasing tracking and enforcement efforts against ransomware operators. Faced with a risk/benefit analysis no longer working in their favor, some cybercriminals shifted targets, leading to double-digit ransomware increases in places like Europe and Asia. Still others are diversifying their tactics.”
The increased focus on cyber risk management in the United States likely “motivated many organizations to create and maintain strong backups and incident response plans, making file encryption less effective than it once was,” perhaps further reducing incentives for perpetrators to target some U.S. sectors, SonicWall noted. For example ransomware attacks targeting higher education actually decreased by 29%, the report said.
Ransomware attacks in all sectors were frequently far more costly and complicated for victims last year, with threat actors using double extortion tactics 120% more often than in 2021, the report said.
Threat actors are also exploiting zero-days vulnerabilities much more, with 35 being actively exploited in 2022, up 150% from the year before.
SonicWall said CISA’s ongoing reporting of common vulnerabilities and exposures continues to help U.S. organizations prevent attacks through timely patching — and it appears patching is being completed more quickly and more broadly: CISA’s list of top vulnerabilities exploited in 2021 only included one “old” vulnerability from the previous year.
“While some of these rankings are undoubtedly due to how much the newer vulnerabilities are being exploited (case in point: Log4Shell), the fact that a majority of the old vulnerabilities on the more recent list are not the same old vulnerabilities that were on the 2020 list suggest that we may finally be seeing some progress on the patching front,” SonicWall said.
One threat vector that saw a decrease in 2022 yet also showed alarming trends for education organizations was malicious intrusion attempts, which fell about 10% overall from the year before and fell 17% among the education targets, SonicWall said.
“However, a rise in the latter half of 2022 in the percentage of education customers being targeted by malicious intrusions prompted SonicWall to project that education customers will continue to see increasing attempts at malicious intrusions,” said the report. The most common form of malicious intrusions recorded last year was Remote Code Executions.
Also growing in 2022 was the worldwide number of PDF-based attacks, which rose 35% over the year before, SonicWall said. Attacks through malicious Microsoft Office files rose by a meager 3% in 2022. Cryptojacking attacks also rose overall and in the education sector — and although the 20% rise in total attack volume last year represented the smallest growth of all sectors, education had the highest percentage of customers targeted, according to the report.
In the report introduction, SonicWall President and CEO Bob VanKirk warned that “new tactics are being developed with breathtaking speed.”
Last year’s shift in cybercrime brought “growth in pure extortion attacks, the fall of ‘Big Ransomware,’ widespread expansion to Linux and cloud targets, the adoption of powerful new languages and platforms, and the growing specter of AI and quantum attacks,” VanKirk said. “ In this volatile threat environment, preparation is more critical than ever before. And today, being prepared means more than just deploying the most advanced solutions. It means developing comprehensive cybersecurity strategies, based on the most current threat intelligence available.”
Download the full report at SonicWall.com.