K12 Schools See Massive Spike in Malware and CryptoJacking in First Half of 2023
- By Kristal Kuykendall
- 08/01/23
Education organizations in the United States are experiencing a “massive spike” in malware, encrypted threats, and cryptojacking so far this year, even as ransomware attacks have slowed, according to SonicWall’s 2023 Mid-Year Cyber Threat Report.
Overall intrusion attempts were up during the first half of 2023 compared to a year ago, with cryptojacking volume breaking all previous records, SonicWall said, as threat actors “shifted away from traditional ransomware attacks in favor of a stealthier means of malicious activities.”
In the first six months of 2023, SonicWall threat researchers recorded 3.7 trillion overall intrusion attempts globally, a 21% increase over the same period a year prior.
The data, though, reveals two divergent trends, the report said: An increase in low-severity intrusion attempts such as pings and other generally benign actions, and a decrease in medium- and high-severity intrusions. These attempts, also referred to as “malicious intrusions,” fell 7% in the first half of 2023, to 5.3 billion.
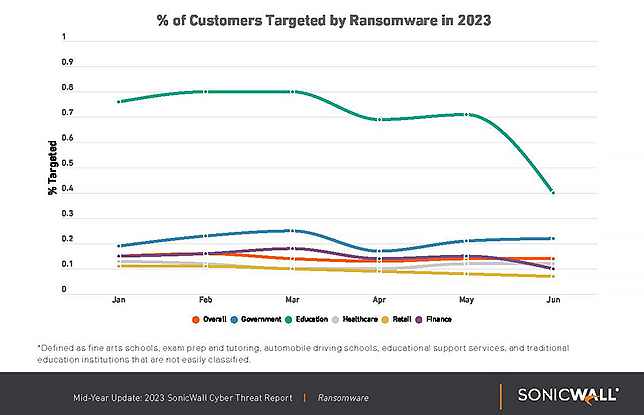
Intrusion attempts targeting education organizations fell by 59% from a year ago, and just over a third of education organizations experienced an intrusion attempt each month in the first half of this year — making education the second-most-targeted industry overall.
The data suggests that threat actors are targeting the education sector at an unprecedented rate – more than any other recorded vertical.
Overall, the United States saw a 49% drop in ransomware attacks during the first six months of 2023, compared to the same period a year earlier.
K–12 schools saw ransomware attacks fall by 19% year-over-year, and SonicWall said every sector except government and higher education experienced fewer ransomware attacks.
But the good news ends there for K–12 cybersecurity practitioners, according to the report.
More Malware, Encrypted Malware
Malware attacks targeting K–12 schools rose by 466% from January through June, compared to the same period in 2022, SonicWall said.
Malware is increasingly being delivered through encrypted means, as well: “Customers working at K–12, higher ed and related education organizations also saw a four-digit spike in malware over HTTPs,” SonicWall said. “Attacks on education customers jumped 2,580% over the same time period in 2022. A corresponding increase in percentage of customers targeted was also observed: about 9.4% of education customers saw an attack in the first six months of 2023, compared with 8.9% a year before.”
IoT malware, on the other hand, fell slightly overall and decreased by 73% in the education sector, the report said.
Cryptojacking is rising exponentially, SonicWall reported, as threat actors seem to be opting for less-threatening ways to earn revenue from their cyber crimes.
In 2022, cryptojacking surpassed 100 million for the first time ever, according to SonicWall. In the first six months of 2023, attack volumes have not only eclipsed that milestone, they’ve more than tripled it, rising 399% to more than 332 million hits — compared to just 66.7 million during the first half of last year.
The education sector saw the biggest jump in cryptojacking, with the number of hits recorded by education organizations rising 320 times year-to-date, SonicWall said.
New Cryptojacking Trends
“Cybercriminals continue to shift away from the quick payout of ransomware in favor of the slower, behind-the-scenes approach of stealing compute power to mine digital currency,” SonicWall said. “To help their chances of success, these cybercriminals constantly shift their tools, tactics and procedures.”
Following are some of the biggest developments in cryptojacking observed by SonicWall in the first half of 2023, verbatim from the report:
-
“Threat actors are quickly shifting from targeting endpoints to targeting cloud services, including one leveraging Kubernetes clusters to mine Dero.
-
“MacOS endpoints have also been in the crosshairs, with cracked versions of FinalCutPro being used to distribute HonkBox cryptojacking malware.
-
“Oracle WebLogic servers are the target of a new crypter known as ScrubCrypt, designed to evade Windows Defender protections.
-
“SonicWall has continued to observe attackers skipping cryptojacking altogether in favor of stealing crypto directly: In late March, we observed a new variant of AsyncRAT designed to steal Bitcoin, Ethereum and Tether.”
Download the full report at SonicWall.com/threatreport.
About the Author
Kristal Kuykendall is editor, 1105 Media Education Group. She can
be reached at [email protected].