Human Error Remains the Leading Cause of Cloud Data Breaches
Human error is still one of the biggest threats to cloud security, despite all the technology bells and whistles and alerts and services out there, from multi-factor authentication, to social engineering training, to enterprise-wide integrated cybersecurity platforms, and more.
That's a conclusion of the 2024 Thales Cloud Security Study, a new report from IT services and consulting company Thales based on a global survey of 2,961 respondents that was fielded in November and December 2023 via web survey with targeted populations for each country, aimed at professionals in security and IT management.
The issue is well known on organizational help desks where troubleshooters have long complained of the PEBKAC problem (Problem Exists Between Keyboard and Chair). But it's also a problem in the cloud, where human errors that have plagued IT for decades are still causing breaches that show little sign of slowing down.
"Human action can compromise security," the report noted. "Fueling this concern is the high number of cloud data breaches, with 44% of respondents reporting such an incident. Fourteen percent reported a breach in the past 12 months. Human error, issues with vulnerability and configuration management, and failures to use Multi-Factor Authentication (MFA) are all cited as leading contributors."
"Identity and Access Management (IAM) is crucial in linking people with technology and policy control," Thales added in a June 26 guest blog post on the site of the Cloud Security Alliance. "People's interaction with technology introduces significant risks, and human error is a leading cause of cloud data breaches."
Noting that almost half of organizations have experienced a cloud data breach, Thales said 31% attributed the breach to misconfiguration or human error, which the company said underscores the need for robust IAM solutions and comprehensive training to mitigate human-related risks. Following misconfiguration/human error, other concerns include vulnerability exploits or failure to implement controls on highly privileged access such as multi-factor authentication (MFA).
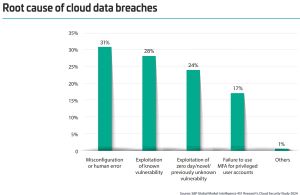 [Click on image for larger view.] Causes of Breaches (source: Thales).
[Click on image for larger view.] Causes of Breaches (source: Thales).
"The impact of human interaction is evident in the types of threats respondents are most concerned about," the report said. "While external attackers and malicious insiders ranked highly, human error — evident in incidents such as unintended actions — was often ranked number one."
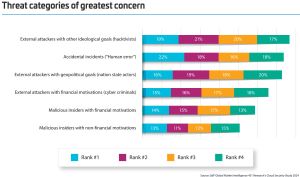 [Click on image for larger view.] Threat Categories (source: Thales).
[Click on image for larger view.] Threat Categories (source: Thales).
As the company's companion 2024 Data Threat Report indicates, the human problem hasn't changed much over the years, nor have attack types (report is from March 2024, data is from S&P Global Market Intelligence's 2021-2024 Data Threat custom surveys):
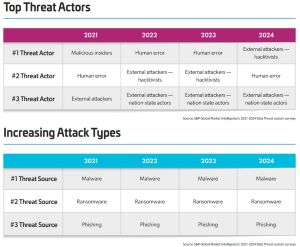 [Click on image for larger view.] Threat Actors/Attack Types (source: Thales).
[Click on image for larger view.] Threat Actors/Attack Types (source: Thales).
"When characterizing threat actors, internal human error remains a critical threat area, always ranking highly, if not the top category," the company's March data threat report said. "In 2024, 22% of respondents said that human error was the single most concerning threat, and 74% of respondents placed some level of priority on threats from human error. The industry must continue redirecting its efforts to more secure and user-friendly approaches.
"Innovations in cloud automation, developer experience, CIAM and workforce IAM reduce human errors and downstream consequences. Malicious adversaries are not only increasing the number of attacks but are also exhibiting growing sophistication in combining techniques. The ecosystems of ransomware creators, access brokers and criminal operators continue to evolve and adapt. While UX improves with new CIAM improvements such as passkeys and password deprecation, new challenges will arise such as deepfake attacks from generative AI. Simplifying this complexity reduces the missteps that adversaries can take advantage of and improves usability and engagement."
Meanwhile, other key highlights of last week's cloud security report as presented by Thales include:
- Cloud security spending now tops all other security spending categories.
- Nearly half (47%) of all corporate data stored in the cloud is sensitive.
- Nearly half of organizations cite it is more difficult to manage compliance and privacy in the cloud vs. on-premises.
- Nearly a third (31%) of organizations recognize the importance of digital sovereignty initiatives as a means of future-proofing their cloud environments.
In its CSA post, Thales advocated for prioritizing proactive security, noting that to better secure cloud environments enterprises should:
- Drive Security Proactivity: Implement proactive security measures to achieve better outcomes, such as ensuring compliance with security audits to reduce the likelihood of data breaches.
- Strengthen Command of New Technologies: Invest in understanding and deploying modern cloud security solutions, such as CNAPP and advanced encryption techniques.
- Foster Developer and Security Partnerships: Enhance collaboration between developers and security teams to address new threats and vulnerabilities.
- Centralize Tools for Decentralized Teams: Provide consistent security tools and controls that enable decentralized teams to manage risks effectively.
"Cloud security is dynamic and complex, and as cloud adoption continues to soar, so do the associated challenges and risks," Thales concluded. "Enterprises can better secure their cloud environments and protect their valuable data by prioritizing proactive security measures, investing in modern solutions, and fostering strong team partnerships."
The 2024 Cloud Security Study is available on the Thales site (registration required).