Tech Allows Workers, Students to Augment Knowledge in the Real World
New location-aware “knowledge injections” or annotations on the EON Reality Augmented Virtual Reality (AVR) platform provide contextual knowledge in real time, helping users to facilitate a manufacturing, maintenance, repair or operation procedure, and other real-world applications.
The EON AR Knowledge Injection functionality taps EON Reality’s artificial intelligence (AI), Internet of Things (IoT) and geopositional tracking technologies to allow users to create AR annotations, such as text, video and voice, linked to the physical world. Alternatively, users can integrate objects from the EON AVR library, from subjects like chemistry or physics. The functionality works with normal tablets and smartphones, or the 3D scanning capability of more sophisticated devices like Google Tango or HoloLens, according to a company statement.
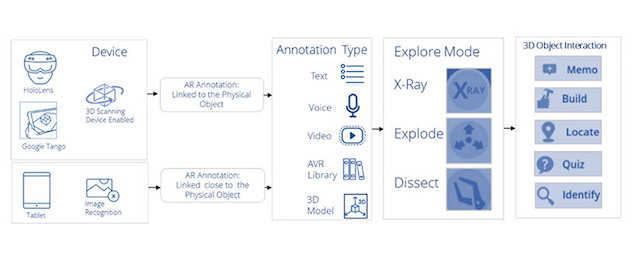
Non-technical users can quickly create or select pre-made text, video and voice annotations on the EON AVR platform.
It is designed with non-technical users in mind, so workers and students alike can use the knowledge injections to complete complex tasks using AR visual cues and instructions. A mechanical engineer, for example, can use the functionality for extra assistance while putting a project together — projecting AR tools onto the materials he is working with. A technician can use the tool to assess a malfunction and find out if a machine needs a particular part replaced. A teacher can prepare an “AR lab” with the annotations, encouraging students to delve deeper into a subject.
The new functionality helps users take context-aware knowledge with them in the field or classroom and instantly “inject” information when needed. It is part of the cloud-based EON AVR platform, which lets users “develop, run, manage, access, store, host and distribute AVR applications without the complexity of building and maintaining the infrastructure associated with developing and augmented or virtual reality app,” according to a company statement. The platform also allows users to use AR as “a visual interface for IoT, builds AR 3D annotations connected with physical objects, and uses artificial intelligence for faster generation of contextual AVR instructions.”
EON Reality has produced standards for AR-based and VR-based knowledge transfer software that supports devices from mobile phones to large domes since 1999. The company said it plans to unveil customer projects based on the new functionality during the first half of 2017.
To see how it works, watch the video below or visit the EON Reality site.
About the Author
Sri Ravipati is Web producer for THE Journal and Campus Technology. She can be reached at [email protected].