Growing Frequency and Rising Costs of Ransomware Attacks on Schools Highlight New Report
2021 Cyber Incidents Disclosed by U.S. Schools is Led By Ransomware for First Time, K–12 Cybersecurity Year in Review Shows
- By Kristal Kuykendall
- 03/10/22
In its annual State of K–12 Cybersecurity Year in Review report released early today, national nonprofit K–12 Security Information Exchange revealed that ransomware has become the most common type of publicly disclosed cyber incident at U.S. schools, as increasingly aggressive tactics by threat actors drive the stakes higher — amid lax government oversight of districts' protective measures and no mandate for districts to disclose incidents to the public.
The data-rich, vendor-agnostic report includes detailed analysis of new cyber incidents as well as identification of trends among the 1,331 publicly disclosed school cyber incidents since K12SIX began the annual report in 2016. It is based on data from the K–12 Cyber Incident Map, considered the definitive source of information about publicly disclosed cyber incidents affecting U.S. public schools and education agencies; the U.S. Government Accountability Office has said the Cyber Incident Map is the “most complete resource that tracks K–12 cybersecurity incidents, including student data breaches.”
During 2021, the K–12 Cyber Incident Map recorded 166 cyber incidents affecting schools in 162 school districts across 38 states — a decrease in publicly disclosed incidents from the two previous years and a finding that will be counterintuitive to many, K12SIX said in its report.
The reasons for the slight decline in disclosed incidents last year is likely due to several factors, K12SIX said:
- The sudden shift to remote learning at the start of the pandemic may have led to a temporary jump in incidents, as the number of devices taken off campuses exploded — as did the vulnerabilities.
- As cyber incidents and ransomware have ramped up in the public education sector, so have costs and minimum requirements for schools to obtain cyberinsurance policies: Districts are being quoted dramatically higher premiums and they’re being required to implement common-sense cybersecurity controls — such as multi-factor authentication for employees — for the first time. “Thanks to this market dynamic and heightened awareness of the cybersecurity challenges facing the K–12 sector in general, school districts may have done a modestly better job of defending their communities from cybersecurity threats during 2021,” K12SIX said in the report.
- School districts are not required to publicly disclose cyber incidents, and requirements for vendors to disclose incidents —where mandates exist — are weak and rarely enforced, the report said. “If it were not for the public-interest reporting of security researchers and investigative reporters during 2021 — employing, e.g., freedom of information requests to compel districts to share incident details they sought to keep from the public eye — the number of publicly disclosed incidents catalogued by the K–12 Cyber Incident Map during the past year would have been even smaller.”
K12SIX noted that because the Cyber Incident Map relies on voluntary public disclosure of cyber incidents, the State of K–12 Cybersecurity report “dramatically understates the scope of the issues facing K–12 schools. ... The true picture is surely bleaker; anecdotal evidence suggests perhaps 10 to 20 times more K–12 cyber incidents go undisclosed every year.”
Types of Cyber Incidents Disclosed by U.S. schools
Since 2016, the K–12 Cyber Incident Map has cataloged a total of 1,331 publicly disclosed school cyber incidents affecting U.S. school districts (and other public educational organizations) across a wide array of incident types, including:
- Student data breaches
- Data breaches involving teachers and school community members
- Ransomware attacks
- Business email compromise (BEC) scams
- Denial of service (DoS) attacks
- Website and social media defacement
- Online class and school meeting invasions
- Other incidents
During 2021, said the report, ransomware incidents were the most frequently disclosed incident type for the first time since the Cyber Incident Map began collecting data.
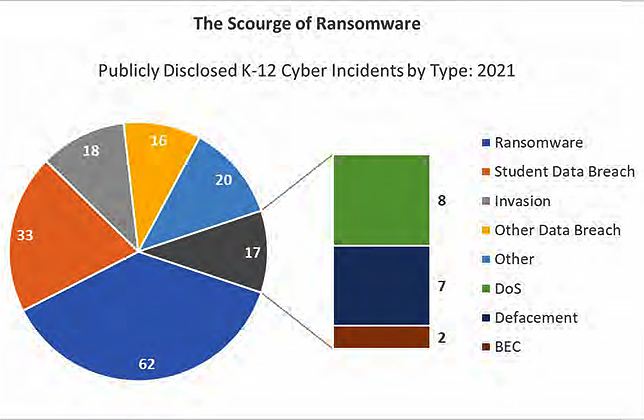
Last year, the K–12 Cyber Incident Map documented 62 instances of U.S. public K–12 school districts impacted by ransomware. These incidents were geographically dispersed, with reports of school ransomware emerging from districts of varying sizes across 24 different states. It was the third consecutive year with more than 50 publicly disclosed K–12 ransomware attacks, the report noted.
While the increasing frequency of ransomware attacks should be alarming to K–12 leaders and policymakers, the evolving — and increasingly damaging and costly — tactics of ransomware gangs are primarily what sets 2021 apart from prior years, K12SIX said.
School districts who do reveal they’ve been hit by ransomware generally do not disclose whether they or their insurer paid a ransom, nor how much a ransom was required by the threat actors.
However, there are exceptions, the report noted: In responding to a June 2021 ransomware attack, a Texas school district told stakeholders that it had paid $547,045.61 to “protect sensitive, identifiable information from being published.”
Even when school districts are able to recover control of their data or networks without paying a ransom, the unexpected remediation costs can be staggering, the report said.
“According to Baltimore County Public Schools officials, the cost of ongoing recovery from a Ryuk ransomware attack late in 2020 grew to nearly $9.7 million dollars one year later. In New York, the Buffalo School Board approved spending nearly $9.4 million on external IT consultants to respond to the ransomware attack it suffered in March 2021.”
Evolving Tactics and Double Extortion
Ransomware attackers’ tactics continued to evolve last year, the report said.
So-called “double extortion” tactics against school districts — first documented in last year’s State of K–12 Cybersecurity report — are now routinely employed against school districts. This method is when ransomware actors steal a district’s data before their malware strain activates its encryption routine, which then gives the attackers the option of demanding two ransoms: one for the provision of a decryption utility, and a second that guarantees verbal confirmation that the attackers deleted the victim’s data from their servers.
The threat actors “can also leverage that data theft to pressure victims — even those that have a robust data backup strategy,” the report said.
“The experience of Weslaco Independent School District (Texas), a late 2020 victim of a ransomware attack, is typical of this double extortion tactic: … The hackers, spurned by Weslaco’s decision to not pay, dumped the files they pilfered on their website. One of those, still posted online, is an Excel spreadsheet titled ‘Basic student information’ that has a list of approximately 16,000 students, roughly the combined student population of Weslaco’s 20 schools last year. It lists students by name and includes entries for their date of birth, race, Social Security number and gender, as well as whether they’re an immigrant, homeless, marked as economically disadvantaged and if they’ve been flagged as potentially dyslexic,” K12SIX’s report said.
Ransomware actors have even resorted to triple extortion of school districts: contacting parents directly to urge them to demand that their districts return to a negotiating table with the attackers.
The most significant source in 2021 of student and teacher data breaches in terms of how many individuals were affected remained vendors and other “trusted non-profit and government partners,” the report said. Last year, districts reported significant breaches of personal information by ACT, PCS Revenue, Student Transportation of America, Independent Health, and the Public School and Education Employee Retirement Systems of Missouri.
“The fact that data breaches and other security incidents continue to plague school district vendors and their partners should raise significant questions about the sufficiency and effectiveness of both industry self-regulatory efforts and existing data privacy and security regulations,” K12SIX said.
Other K–12 Cyber Incident Types Disclosed During 2021
While ransomware and data breach incidents are more frequently experienced by school districts, they routinely fall victim to a wide array of other types of incidents. The most common of these include:
- Business email compromise (BEC) scams: Involving the use of email to scam school business officials and staff members out of sensitive information and/or millions of dollars of money, including by issuing fake invoices to districts, by redirecting authorized electronic payments to bank accounts controlled by criminals, and by stealing W-2 tax information of district employees.
- Online meeting and class invasions: Involving unauthorized access to online classes and K–12 meetings for the purpose of disruption — often by hate speech; via the sharing of shocking images, sounds, and videos; and/or, threats of violence.
- Email invasion: Involving the compromise of a school district’s email systems by unauthorized individuals for the purpose of bulk sharing of or links to disturbing images, videos, hate speech, and/or threats of violence to members of the school community.
- Website and social media defacement: Involving unauthorized changes, such as posting inappropriate language and images, to a school website or official social media account.
- Denial of service attacks: Intended to make school IT resources unavailable to students and staff by temporarily disrupting their normal functioning.
Although risk management is a core task of local school governance, the absence of meaningful cybersecurity standards for schools at either the state or federal levels — coupled with a shortage of resources for meeting any such standards — “all but guarantees that many districts will continue to place the safety and security of students, teachers, and community members at avoidable risk,” K12SIX said.
To view or download the full report, visit K12SIX.org/the-report.