Online instruction provider VHS Learning has added 11 new courses for the 2023–24 school year for high school students studying online either through their local school district or at home for supplemental learning, the nonprofit said in a news release.

A new bill filed in both houses of Congress Wednesday by U.S. Rep. Doris Matsui (D-CA), Rep. Zach Nunn (R-IA), Sen. Marsha Blackburn (R-TN), and Sen. Mark Warner (D-VA) would direct CISA to create a cybersecurity information exchange for K–12 schools, a voluntary incident registry, and a “Cybersecurity Technology Improvement Program” funded at $10 million per year for the next two years.
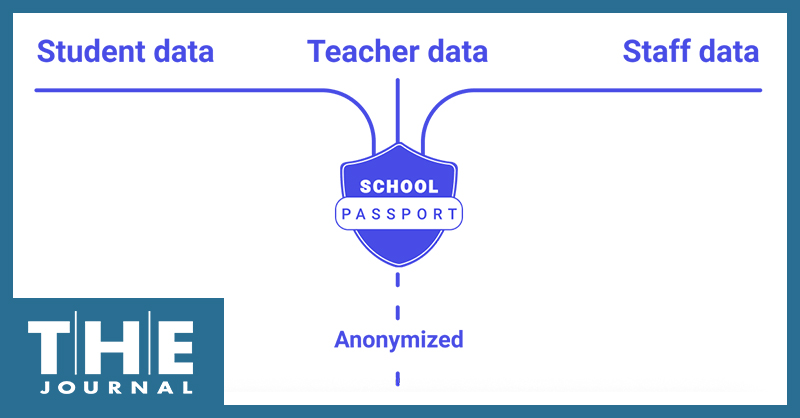
Global Grid for Learning has unveiled its newest school data exchange solution designed to give schools better data analytics and control over data privacy while eliminating the need for vendors using the standards to access and share students’ protected private information, by using patented anonymization and API technology.
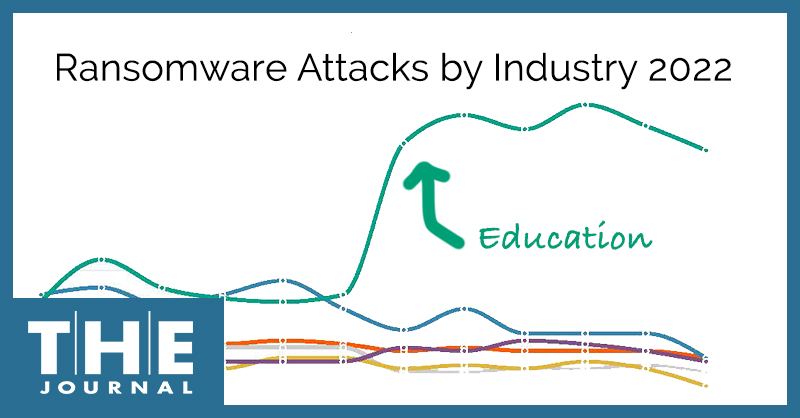
Ransomware attacks targeting K–12 schools worldwide last year grew at an “absolutely massive” rate of 827% over 2021, according to SonicWall’s 2023 Cyber Threat Report, and the data shows that education customers — those whose data is compromised during ransomware attacks — had the highest percentage reporting ransomware attempts of all sectors studied.

In the past week, CISA has published alerts on seven known exploited vulnerabilities — two of which put a long list of Apple devices at risk — ordering federal agencies to remediate the identified vulnerabilities immediately and encouraging all organizations to do the same.
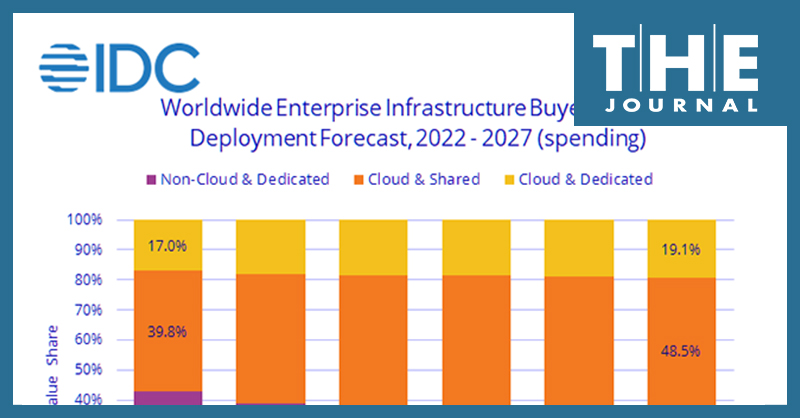
Worldwide IT spending is projected to increase 5.5% this year to a total of $4.6 trillion by the close of 2023, according to the latest forecast by market researchers at Gartner, while IDC analysts detailed a decline in spending on non-cloud infrastructure and devices but project significant growth in cloud infrastructure spending.
Two prominent education technology-focused associations have teamed up to ask the Federal Communications Commission to extend service delivery dates for the Emergency Connectivity Fund.
A Funds For Learning E-rate expert shares what K–12 procurement officers and IT leaders need to know so they can be prepared to apply for the expanded funds if and when the FCC decides to expand the E-rate eligible services list — particularly if the expansion plan of choice means that the amount of E-rate funds to cover modern cybersecurity services is limited, at least for the first few years.
A technology educator shares how her nonprofit is using ChatGPT to help students participating in Technovation programs go further in their brainstorming and ideation as they aim to develop AI-based solutions to real-world problems. Here’s a concrete example from our program: Students in one group were interested in developing technology-based solutions to food wastage and conservation, encouraging more students to read, exercise, and be more inclusive.
Blackbaud, a South Carolina-based provider of administrative, donor management, and CRM software to education and nonprofit organizations, has been fined $3 million by the U.S. Securities and Exchange Commission "for making misleading disclosures about a 2020 ransomware attack that impacted more than 13,000 customers,” the federal agency said.