Free Tool Lets Schools Test Encryption of Ed Tech Software
- By Dian Schaffhauser
- 02/14/17
Common Sense Education has made its encryption-checking tools available as open source so that anybody can check out the security settings of education technology products.
The release of its security scanning scripts follows on a project to check over the encryption practices of technology commonly used within schools. That effort, undertaken in October 2016, found that a "significant number" of companies don't provide even the most basic support for encryption.
Encryption is the process of converting data into a form that's unreadable by anybody but the user who holds the code needed to reverse the encryption. Transport Layer Security (TLS), sometimes referred to as Secure Socket Layer (SSL), is a set of technologies that protect the security and privacy of internet communications; and it uses encryption to prevent information from being read on the network by unauthorized viewers. For example, if a student is working on homework at a WiFi hotspot, anything sent without encryption — such as a user name or password — could be captured through snooping and freely read by others on the same network.
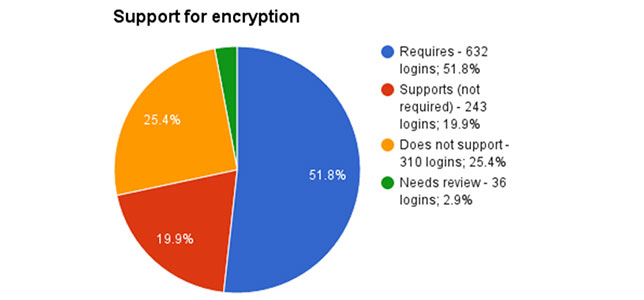
For the testing process, the non-profit ran automated tests on 1,221 logins used by 1,128 vendors that have products in schools all over the country. The testing excluded sites that don't require a login, that are no longer in business or that for "whatever technical reason" didn't load properly. Slightly more than half of the resulting companies (52 percent) require encryption; 25 percent don't support it at all; and another 20 percent don't require an encrypted connection.
Interestingly, Common Sense Education found that one well known vendor enables encryption in districts in states where laws require "reasonable security" and avoids it in some districts in other states where the laws aren't as rigorous. Another product intended to be used by students of all ages supports encryption in some product offerings and not in others. And "multiple" companies take a request for an encryption connection and redirect it to an unencrypted connection.
Currently, the company hasn't released a list of the vendors tested or their individual results, preferring to keep the findings in aggregate to give companies a chance to improve their encryption practices. However, the organization has stated that it will rerun the survey with the hope of seeing an increased use of encryption.
Even then, though, Common Sense would also like people to be able to run the tests themselves. That's why the testing code has been made available as an open source project. As Bill Fitzgerald, director of its privacy initiatives, wrote in a blog article, "It's not complicated." The GitHub repository where the code is available includes documentation that describes how to check individual URLs and even "batch-process hundreds or thousands of URLs."
As Fitzgerald recommended, "If you're a vendor, we strongly recommend that you use this script to check the login URLs of your products. If you're in a school or district, use this script as part of a quick triage when you're evaluating technology."
About the Author
Dian Schaffhauser is a former senior contributing editor for 1105 Media's education publications THE Journal, Campus Technology and Spaces4Learning.