Vulnerabilities in Edulog Portal Revealed Bus Location Data, Parent Logins for 6M Students
Researchers Warn Schools to Stop Publicly Posting Edulog Sign-Up Codes
- By Kristal Kuykendall
- 12/14/23
Security researchers said this week that API vulnerabilities in the Edulog school bus tracking platform made the names and geolocation data of 6 million student riders available to anyone, and while the vulnerability has been fixed, schools that post their Edulog sign-up code on their websites are still at risk.
Tenable Research, in an advisory posted Dec. 13, said it first discovered the security problems in Edulog’s Parent Portal apps in September and notified the company; researchers created a free account without a school access code and were then able to access the API endpoints directly, rather than relying on the apps.
“They soon realized that the access control measures in place were client-side restrictions enforced only by the apps themselves,” Tenable wrote on its blog. “By submitting requests manually, they had seemingly unfettered access to any information that could be obtained via the Parent Portal API.”
In their tests, researchers gained access to student riders’ names and assigned bus routes, parent contact information, GPS data, and configuration details — such as usernames and encrypted passwords for third-party integrations — for individual school districts, Tenable said.

Edulog, short for Education Logistics, provides school bus routing and tracking services to thousands of school districts throughout the U.S., stating on its website that 6 million students are transported on over 85,000 buses routed by Edulog software.”
Its Parent Portal and Parent Portal Lite apps give parents and school staff real-time information on school buses’ current locations, pick-up and drop-off times, and notifications about delays or route changes.
Typically, parents or school staff of districts using Edulog can sign up for a free account for the Parent Portal apps; a registration code is required to obtain access to bussing information for a particular school or district. These registration codes are provided to parents and staff by the schools themselves; Tenable noted that some schools post the codes on their websites or in publicly available documents intended for parents.
Tenable said it reported the issues to Edulog on Sept. 13, 2023, and that by Nov. 30, Edulog responded that “all reported issues have been resolved.” When asked about its plans to disclose the exposed data to its users, on Dec. 11 “Vendor states that they will not be posting an advisory of their own,” Tenable wrote.
While there is no indication the exposed data was accessed or misused prior to the fix, Tenable emphasized that districts should not make their sign-up codes publicly available.
“For example, even without the vulnerabilities discovered in the Parent Portal services, there isn’t necessarily anything stopping a malicious actor from signing up for an account and obtaining a registration code for a given school through other means. The actor could ask another parent, call the school and pretend to be a parent, or simply search for one on the internet:”
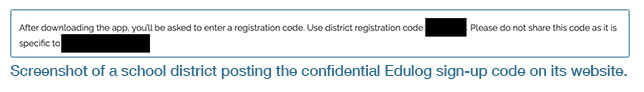
The security advisory noted that similar issues are “common in industries where the concept of data security is often conflated with compliance standards. In fact, it’s likely that much of the information that could have been obtained via the Parent Portal API, such as names and addresses, was already considered open data and complied with regulatory requirements.”
Tenable said that while Edulog took their report seriously and provided fixes in a timely manner, “all those involved – Edulog employees, agents for the school districts, and parents using the services – are responsible for making sure the data relating to these services is handled properly.”
Read the full security advisory at Tenable’s website.
About the Author
Kristal Kuykendall is editor, 1105 Media Education Group. She can
be reached at [email protected].