LiveTime Service Desk Software Now Out for Android
- By Dian Schaffhauser
- 09/10/12
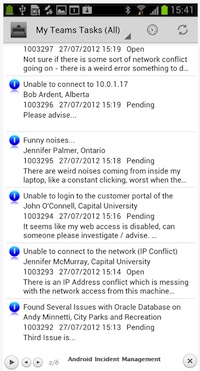
LiveTime service desk software on Android |
LiveTime, a company that specializes in applications for service management, has developed a version of its software as a native app for Google Android. Available in Google's marketplace, Google Play, the new app allows IT staff to access service requests from their mobile devices. LiveTime had released a comparable iPhone client in March 2011.
CT and THE
LiveTime Service Desk Software Now Out for Android
A company that specializes in applications for service management has developed a version of its software as a native app for Google Android. Available in Google's marketplace, Google Play, the new app from LiveTime allows IT staff to access service requests from their mobile devices. LiveTime had released a comparable iPhone client in March 2011.
LiveTime's product line consists of software to manage the functions of the service desk and help desk, as defined by ITIL 3 best practices. The Information Technology Infrastructure Library (ITIL) is a set of practices that guide the lifecycle of IT services to better align with the needs of the organization.
LiveTime Service Manager and Help Desk software provide a single point of contact for end users to communicate with the help desk when a problem or question surfaces and provides a way for the IT team to manage the request, changes, deployment, configuration, and knowledgebase adjustments. The applications are available in both on-premises or software-as-a-service versions and include reporting and dashboards; OpenID authentication to enable users to log in via an existing Google or Yahoo account to track their support tickets; language localization; and the ability to communicate with users via email or text;
The mobile apps let the technician manage service requests and the activities around that remotely. They also provide a way for the staff person to communicate with customers and monitor adherence to service level agreements.
Features of the Android app edition include:
- Geolocation mapping of customers;
- A service metrics dashboard;
- Request filters;
- A request history;
- The ability to add notes and time to requests; and
- Management of requests, incidents, problems, changes, and release management.
LiveTime software is in use by the School District of Philadelphia, Lincoln Public Schools in Nebraska, and Charlotte County Public Schools in Florida, among others.
About the Author
Dian Schaffhauser is a former senior contributing editor for 1105 Media's education publications THE Journal, Campus Technology and Spaces4Learning.