Red Cedar Solutions Group has launched a new platform called Stepwell, a district-level system that provides insights for special education compliance and monitoring.
In preparation for new school safety laws taking effect this summer and fall, compliance software PublicSchoolWORKS has updated its EmployeeSafe Suite and StudentWatch Suite to guide K–12 safety and compliance leaders through the various new state and federal reporting requirements, according to a news release.
Hardware-enabled collaboration provider Airtame has boosted its partnership with unified communications software developer Rise Vision to expand K–12 schools’ ability to display emergency alerts and school messaging across Airtame-connected devices, according to a news release.
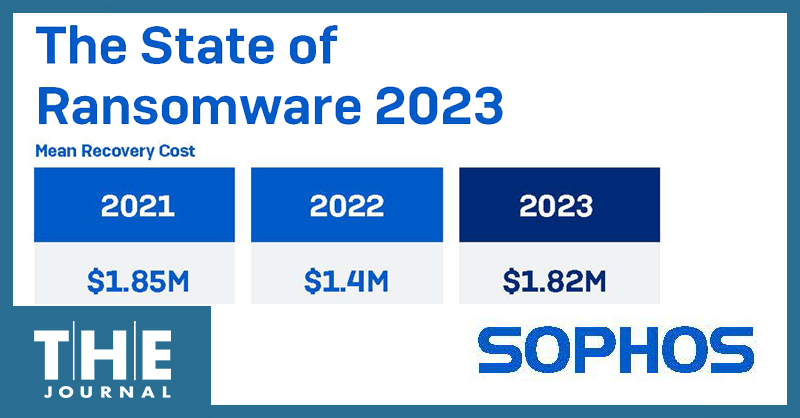
Eight out of 10 K–12 school districts surveyed for Sophos’ 2023 State of Ransomware Report said they were hit by ransomware last year — a 43% increase from the previous year’s results — making the K–12 education sector the most-popular ransomware target in the world in 2022.
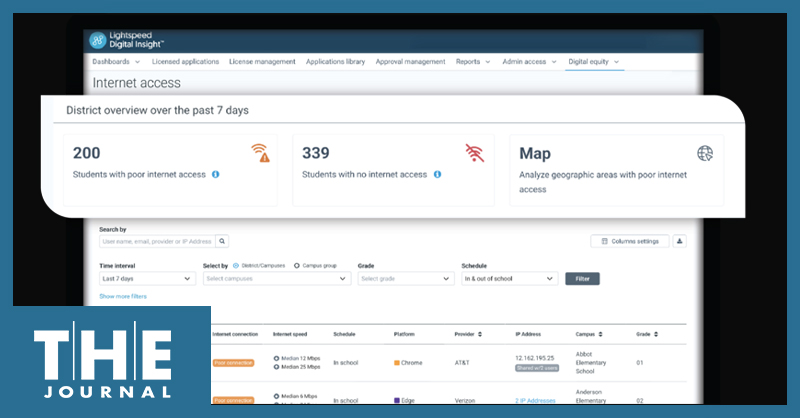
The new Digital Equity module, an extension to Lightspeed's Digital Insight network and ed tech analytics platform, provides real-time connectivity and device health data on students’ school-issued devices, enabling school leaders to know when students experience connectivity outages at home — allowing for interventions or assistance before learning outcomes are impacted, the company said.

Recent leadership and advisory roles announced by education and ed tech organizations include a new CEO at Pearson, a new CMO at D2L, a new COO at Centegix, a new board member at United Educators, a new CEO at National Math and Science Initiative, a new CEO at Mentor, and new special education advisory leaders at BlazerWorks.

Cybersecurity nonprofit K12 Security Information Exchange is inviting K–12 IT and network security practitioners to submit their input and feedback for the upcoming 2023–24 edition of the K12 SIX Essential Cybersecurity Protections Series of guides for public schools’ risk management efforts.
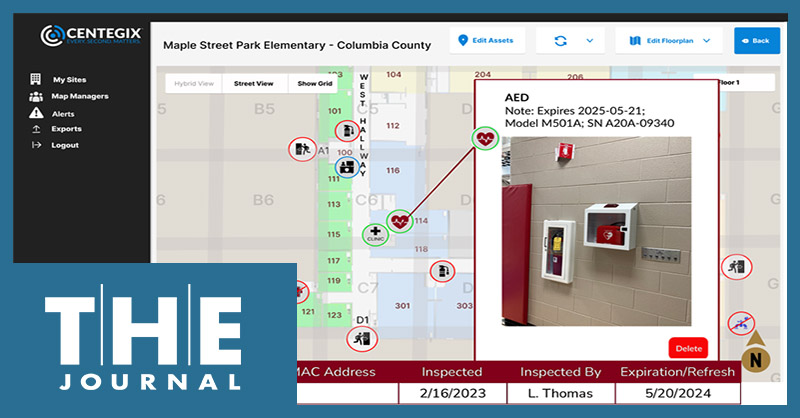
Incident response software provider Centegix has introduced a digital mapping solution called Safety Blueprint that provides a “dynamic, multi-layered map of all campus facilities and spaces, including the precise location of all safety assets,” to help district leaders plan better incident management and emergency response, according to a news release.
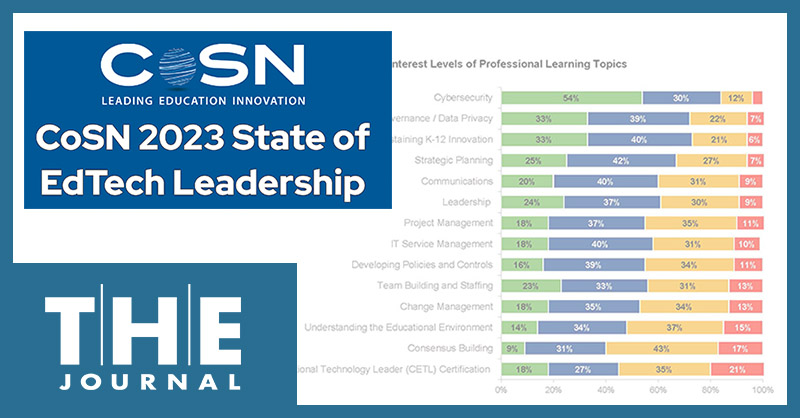
CoSN’s 10th annual State of Ed Tech Leadership report released this week shows some things remain the same — K–12 technology leaders need more resources to keep up with technological innovations in schools — while priorities since the survey began have shifted remarkably.
Facilitative leadership can help academic communities support success and promote holistic outcomes. The timing for this type of approach is especially important as schools look to re-energize staff, restore trust, and find new ways to support the changing needs of students in today’s post-pandemic learning environment.